

October 07, 2014
Shellshock is a security bug in Bash (Bourne Again SHell) command-line interpreter, mostly known as shell. Linux expert Stéphane Chazelas revealed this bug on 24th September 2014, and it is more severe than Heartbleed bug. Shellshock allows attackers to gain unauthorized access to computer system by executing arbitrary commands and it is officially documented as CVE-2014-6271 and CVE-2014-7169.
Who is Vulnerable?
Theoretically all systems using bash are vulnerable, but most systems connected to the internet are exposed to remote exploitation. Linux and Apple's OSX (since 10.3) which uses bash as default command line interpreter are highly vulnerable. Generally in Windows, system bash is not the default interpreter but if the user changes bash as default interpreter, then it is also vulnerable.
Where bug occurs?
This bug is found under Bash's parsing code which unintentionally executes commands when concatenated, to the end of function definitions that are stored in the values of environment variables.
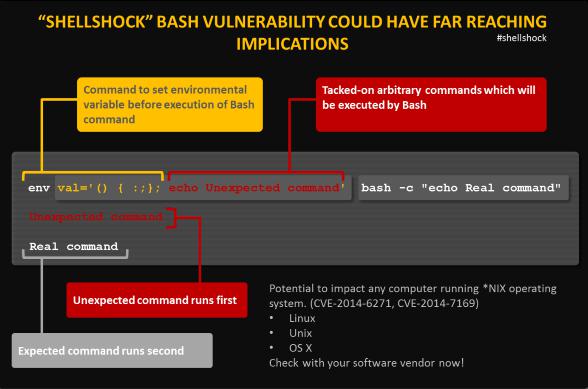
[Image reference: https://www.symantec.com/connect/blogs/shellshock-all-you-need-know-about-bash-bug-vulnerability]
How it makes vulnerable?
An attacker who has access to a remote vector, will be able to remotely inject Bash commands on the system without any kind of authentication and enables the hacker to process all tasks with the attacked system that a normal user could do.
How attacker exploiting it?
HTTP Servers
The most attack and targets are pointed towards HTTP web servers. Servers that run on Common Gateway Interface (CGI) or FastCGI have the capability to expose Bash to a HTTP request. A maliciously crafted HTTP request allows the attacker to inject arbitrary commands onto the server with Bash invoking it to execute them. Bash can be called directly by the CGI (i.e. A Bash script), or could be called via a sub-process and system command. If Bash is started within the context of this malicious CGI request, the vulnerability gets triggered.
For example, CGI could execute a PHP script, which includes a call to system. When this is triggered over a system having Bash as the default shell, it leads to vulnerable attack.
DHCP
In this type of attack Apple OSX is unaffected. The DHCP client with LINUX and UNIX system uses Bash to configure the network interfaces. This attack can be exploited when the system connects to a malicious DHCP server. The vulnerable DHCP client will use variables provided by DHCP server and save them under environment variables. This generally happens when the user tries to connect to DHCP server through public wi-fi access points.
SSH
Mostly SSH requires a user for authentication privileges in accessing the commands. The BASH is capable of overcoming the restriction with privileged escalations.
CUPS (Common UNIX printing System)
CUPS is a print server commonly used with Linux and Unix systems. On processing filters CUPS uses user controlled variables to set environment variables. This makes it vulnerable when CUPS initializes Bash during its process.
How to fix?
By upgrading to the latest version of bash, it can be fixed using the following commands for CentOS and Red Hat Linux
“yum update bash”
How to test?
To check the vulnerability of the system, the following commands could be used:
CVE-2014-6271 Vulnerability check
Execute the following command in terminal
“env 'x=() { :;}; echo vulnerable' 'BASH_FUNC_x()=() { :;}; echo vulnerable' bash -c
"echo test".
If output contains the word 'vulnerable' , then system is vulnerable.
CVE-2014-7169 Vulnerability check
Execute the following command in terminal
“cd /tmp; rm -f /tmp/echo; env 'x=() { (a)=>\' bash -c "echo date"; cat /tmp/echo”
If system is not vulnerable, it will produce the following output.
#cd /tmp; rm -f /tmp/echo; env 'x=() { (a)=>\' bash -c "echo date"; cat /tmp/echo
date
cat: /tmp/echo: No such file or directory
If its vulnerable, then it will produce the following output
#cd /tmp; rm -f /tmp/echo; env 'x=() { (a)=>\' bash -c "echo date"; cat /tmp/echo
bash: x: line 1: syntax error near unexpected token `='
bash: x: line 1: `'
bash: error importing function definition for `x'
Other CVE'S of Shellshock
1. CVE-2014-6277 and CVE-2014-6278 relates to the parsing of function definitions in environment variables by Bash. It was discovered by Michal Zalewski.
2. CVE-2014-7186 and CVE-2014-7187 relates to an out-of-bounds memory access error in the Bash parser code. While working on patching Shellshock, Red Hat researcher Florian Weimer found this bug.
Fix for LINUX:
The following are the links that could be used in accessing the patches and fixes appropriate to the OS, dated 24th September 2014.
1. Debian—https://www.debian.org/security/2014/dsa-3032
2. Ubuntu—https://www.ubuntu.com/usn/usn-2362-1/
3. Red Hat—https://access.redhat.com/articles/1200223*
4. CentOS—https://centosnow.blogspot.com/2014/09/critical-bash-updates-for-centos-5.html
5. Novell/SUSE— https://support.novell.com/security/cve/CVE-2014-6271.html
Fix for Apple OSX Systems
Being aware of the risks, Apple has released the patches to fix OS X's vulnerability to the Shellshock bug, dated 29th September 2014.
Patch can be downloaded from the following links.
1. Mavericks: Bash Update For OS X Mavericks
2. Mountain Lion: Bash Update For OS X Mountain Lion
3. Lion: Bash Update For OS X Lion